Advertisement
Google Ad Slot: content-top
Spring Boot JWT (JSON Web Token)
What is JWT?
JWT (JSON Web Token) is a compact, URL-safe means of representing claims to be transferred between two parties. It is commonly used for stateless authentication in APIs.
How JWT Works?
1️⃣ User logs in → Sends username & password
2️⃣ Server validates credentials → Generates a JWT token
3️⃣ Token is returned to the client
4️⃣ Client sends token in Authorization header in each request
5️⃣ Server verifies token before allowing access
Add JWT Dependencies:
Add the following dependencies in pom.xml:
Configure JwtService Class:
Create a Service class to generate & validate JWT tokens.
Create a User Entity:
Implement User Repository:
Implement UserDetailsService for Authentication:
Create JWT Authentication Filter:
Configure Security:
Create Authentication Controller:
Testing the REST API with Postman:
Once the application is running, test the endpoints:
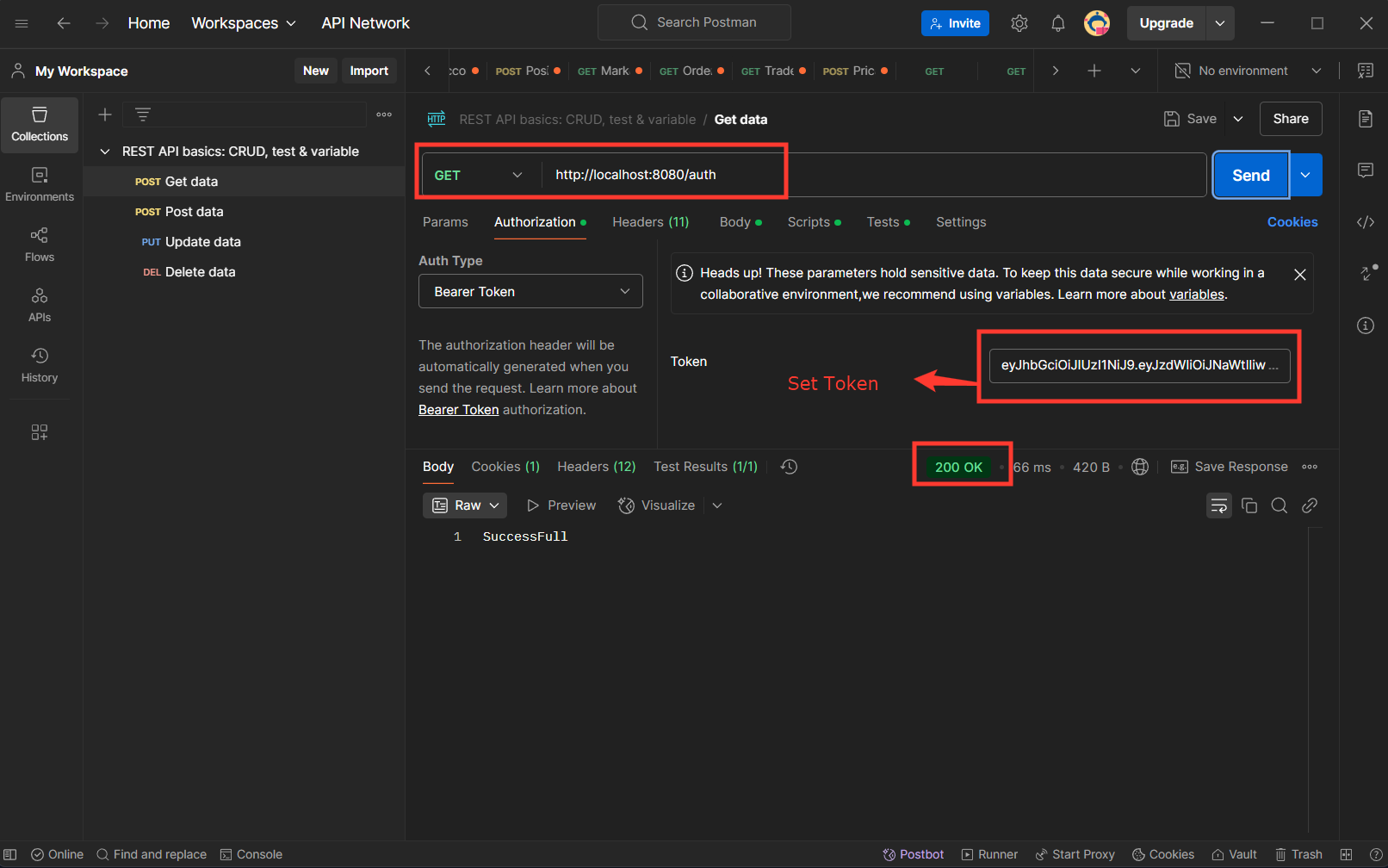
Register User POST:http://localhost:8080/register
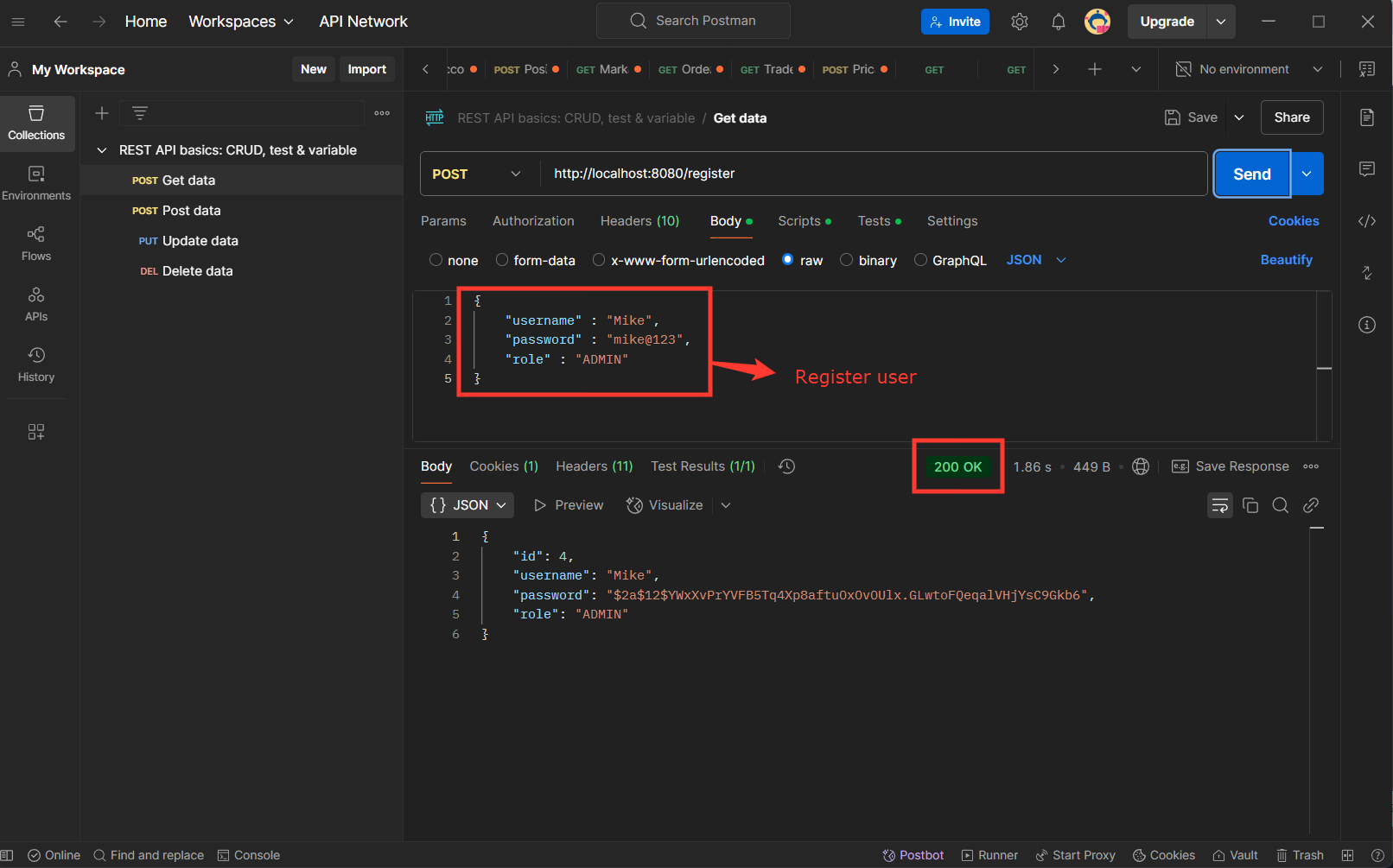
Login User GET:http://localhost:8080/login
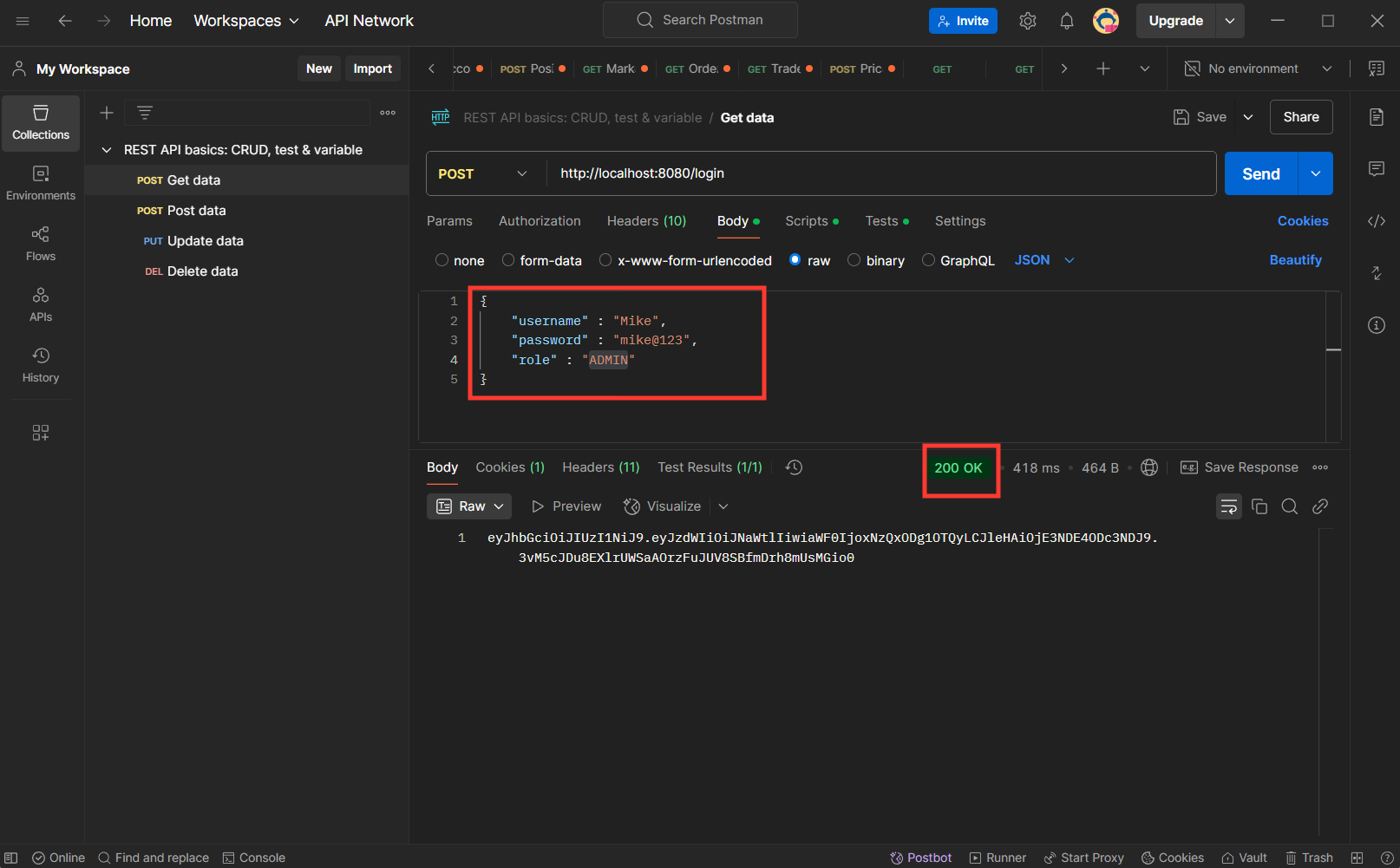
Set Token for other Route GET:http://localhost:8080/auth